Introduction
Did you know that HPE NonStop systems are present in over 50% of the Global 500 banks, at some of the largest retail payment processors in the world, and over 75% of the Global Telcos?
If we look at the kind of applications that run on HPE NonStop systems, it quickly becomes apparent that high volumes of mission-critical, sensitive data are routinely processed on HPE NonStop servers. Organisations in the financial industry use them to run core banking, RTGS, trading and payments systems round the clock.
The majority of payment transactions around the world touches a NonStop system at some point in the payments value chain, and it is this PAN (Primary Account Number) data that needs to be protected adequately.
Data breach attempts have become, unfortunately, a daily event for almost any organisation that processes valuable data and pose a significant threat to many businesses. Increasing pressure from ever-tighter data privacy rules and regulations (PCI DSS, HIPAA, and GDPR to name a few) combined with painful fines for non-compliance put the spotlight on enterprise data protection.
The case for data-centric security
Unfortunately, the perimeter and layer defences companies put in place to deter or fend off malicious attackers are not sufficient anymore.
As news headlines continue to demonstrate, attackers are still getting through the perimeter security defences, and it takes several months on average before breached companies even notice that their data has been compromised.
Data-centric security protects the ultimate target for hackers – your valuable data.
Security on the perimeter of your organisation is still essential, but when (not if) hackers manage to bypass the perimeter security, they gain access to mission-critical data. That data is precious to the hackers, and a breach of such data can be very damaging for the affected organisation.
It needs to be ensured, therefore, that when data falls into the hands of attackers, it is secure and worthless to them. That is why you need to have a data-centric approach, which removes the value from the data and yet allows you to process and exchange the data securely within the enterprise or with trusted partner organisations.
Organisations need to protect sensitive data when stored in files, database tables, or anywhere on HPE NonStop systems. Only data-centric protection ensures that the data itself is protected and not left in a vulnerable state. Adequate data-centric protection reduces the risk of data exposure and minimises the need for compensating controls when reviewing data protection regulations.
Protect data early on
Good data protection practices (the ‘golden rules’ of data security if you like) say that you need to protect your data as soon as possible and unprotect it only if necessary. The picture below shows an example of how the data is protected (tokenised) early on in the process, how it is being used for further processing and data management, and how it is being unprotected for external communication or internal customer services functions.
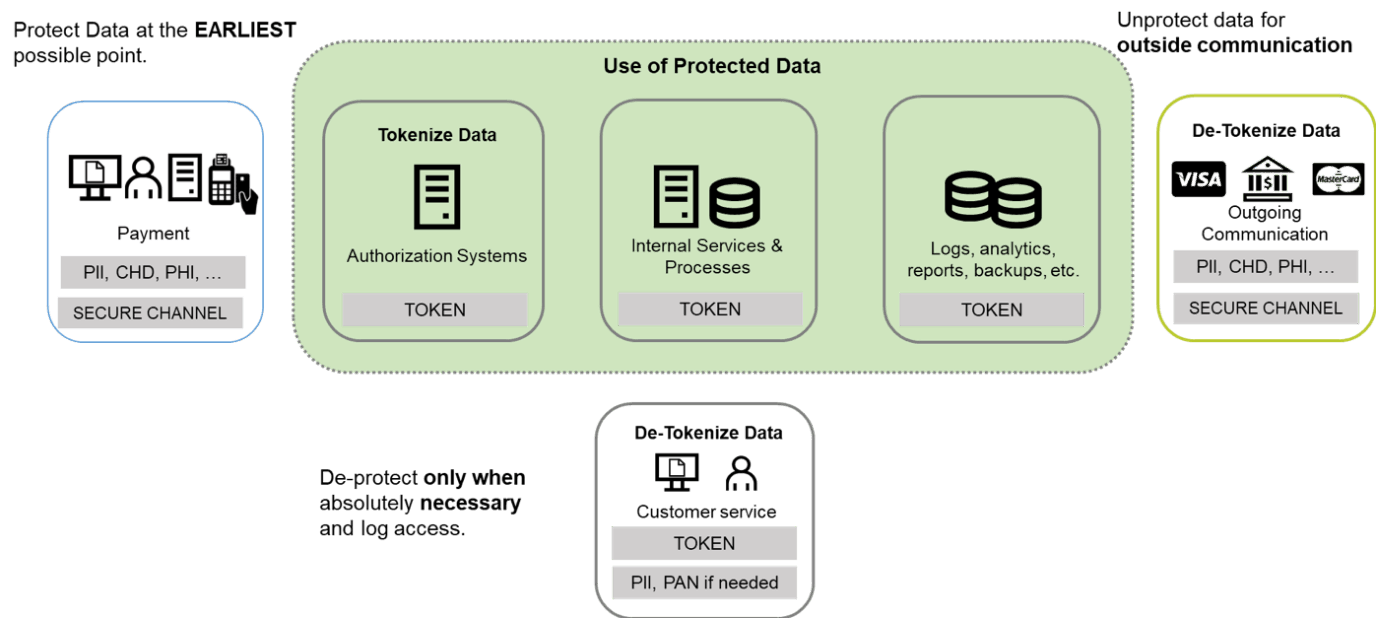
This puts HPE NonStop and the data being processed and stored at the centre of an effective enterprise data protection strategy. At the same time, it makes HPE NonStop systems the obvious starting point for any data protection project.
But how do you secure your business and protect your mission-critical data?
As modern businesses across all verticals continue their rapid digitalisation, the need to store, process and exchange data securely is becoming an essential business continuity factor for any company. Although some industries have been subject to strict data privacy regulations for decades, such as financial transactions or healthcare organizations, the introduction of much broader data protection regulations like GDPR has put massive pressure on just about any organisation that has to store and process personal data.
Data-centric security might be simple in theory – just protect the data at its source instead of securing each piece of infrastructure separately. However, its successful deployment critically depends on the solution’s capability to enforce the same security and compliance policies consistently across all systems (be it on-premises servers, cloud services, databases, mainframes or anything else) and the effort required to integrate it with existing modern and legacy applications.
The best way to address these challenges is to deploy a highly scalable and fault-tolerant data protection platform that utilises tokenisation technology to replace sensitive information in various data sources with non-sensitive equivalents, which have no exploitable value. By ensuring that existing business applications are operating on tokenised data instead of original information, businesses can successfully reduce the risk of data breaches or unlawful exposure as well as ensure regulatory compliance. Together with encryption, data tokenisation has long been one of the recommended data protection technologies under such frameworks as PCI DSS, ASC X9, and GDPR (among others).
As opposed to traditional encryption, however, tokenisation methods are format preserving (thus not breaking the functionality of legacy applications), can be flexibly configured to support partial anonymisation, and require substantially less computational resources. These properties have made tokenisation solutions very popular for high-performance but highly regulated environments where sensitive data, like financial transactions, criminal records or stock trades are processed.
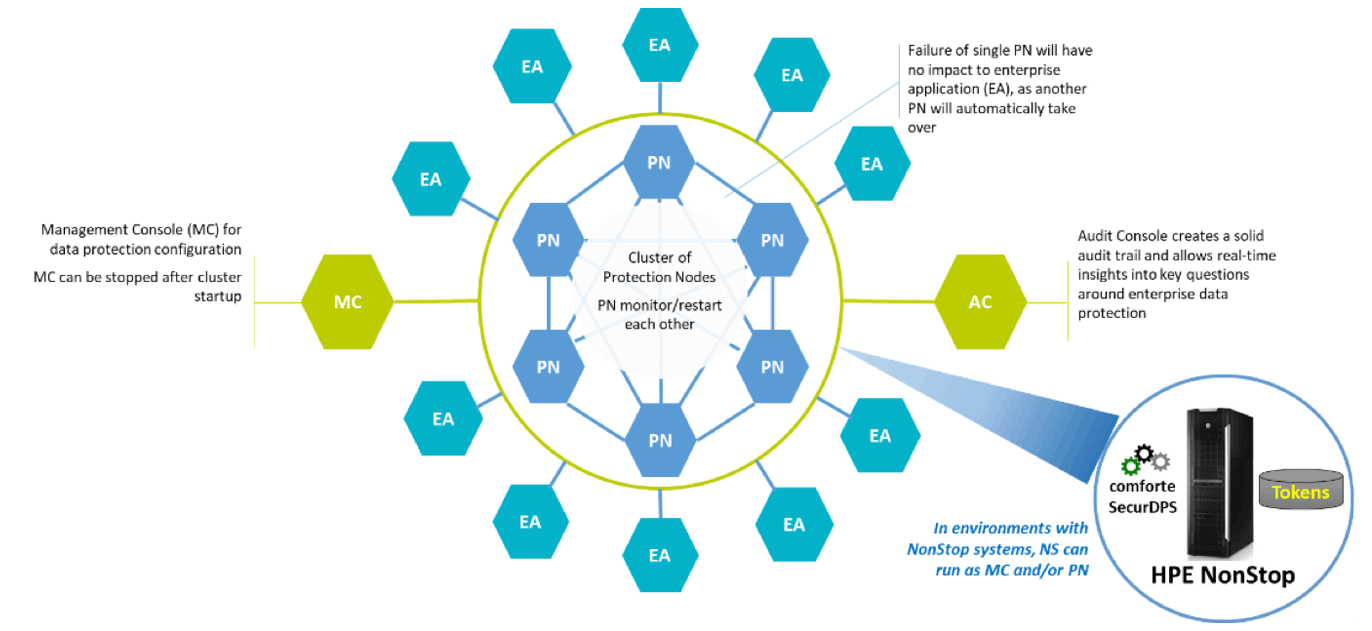
Robust and flexible architecture is key
To deploy data-centric security, you need a tokenisation solution with a robust, modern architecture that can be implemented in different environments depending on your business requirements. Implementations on-premise, in the cloud or a combination of both need to be supported to provide flexibility in line with your cloud strategy.
In the picture above, the tokenisation solution runs on an HPE NonStop system, which adds high availability, fault-tolerance and transaction integrity to the data protection setup. A cluster of protection nodes provides the tokenisation of the data. Failure of individual protection nodes will have no impact on the enterprise application as another protection node will take over immediately. The management console is provided for the configuration of your specific data protection requirements, and the audit console creates an audit trail giving insights into fundamental questions around enterprise data protection. But what does it look like in the real world?
A customer case study
Tokenisation of your mission-critical data like PANs not only strengthens your enterprise security generally, it also helps to comply with industry standards and data privacy rules and regulations. The following section describes how a global payment service provider achieved PCI compliance and protects the data of its customers via tokenisation.
This American multinational payment service provider offers one of the most advanced and ubiquitous payment processing networks in the world. It securely handles the private data associated with billions of credit and debit cards and processes tens of thousands of transaction messages per second. This vast, high-speed network facilitates electronic funds transfers from nearly 50 million merchant locations, over a million ATMs and more than 15,000 financial clients across every continent in the world except Antarctica. With such a large network managing such a large volume of transactions, it is vital that data can be kept secure and still flow quickly between platforms across the network.
To protect their customers’ data and comply with data privacy regulations like PCI DSS and GDPR, the company decided to look for a proven data protection solution.
Download the case study to read how this payment service provider implemented a state of art solution that:
-
- did not interrupt or affect their service levels
- was far more affordable than the customer had expected
- enabled the customer to secure their data in
Conclusion
HPE NonStop systems are at the heart of many mission-critical businesses around the world. In particular, in the financial services industry and the payments industry. The nature of a payment services provider’s business necessitates that they process a lot of sensitive data, i.e. valuable PANs. There is an inherent need to protect the data fuelled by an increasing number of damaging data breaches and a tighter net of data protection and data privacy rules and regulations. The best way to do so is by applying a data-centric approach with tokenisation as the recommended technology.
Deploying a tokenisation solution on HPE NonStop strengthens the NonStop platform in the enterprise as it protects the data at its source and helps to keep the data safe further downstream in the process.
To learn more about enterprise data protection, go to …




Be the first to comment