
The Ransomware Menace
Ransomware is a concern across all industries. High-profile attacks make headlines and cause substantial disruptions. The reason these attacks are successful is often inadequate monitoring and a broad attack surface. Many organizations fail to implement best practices such as multi-factor authentication (MFA), change management, and proper access controls. This lack of stringent security measures makes it easy for attackers to use social engineering to walk through the front door, gain a foothold, and deploy ransomware.
Take the example of MGM Resorts, which faced a massive ransomware attack in September 2023 that led to MAJOR operational disruptions. MGM’s ordeal began when hackers used social engineering to trick the company’s tech support into granting them network access. The attackers posed as legitimate employees, using stolen and harvested information to convince support staff to reset passwords and grant access. Once inside, the attackers breached system after system due to improper security configurations, too much privilege, unpatched systems, and many more security missteps. Once their beachhead was established, the hackers demanded a ransom of $30 million, or they would launch a full-scale ransomware attack. MGM opted not to pay the ransom, so the attackers kept their promise and launched the attack against MGM’s network. MGM had no choice but to take its systems offline to contain the scope of the attack and opted to rebuild its IT environment.
 This breach resulted in MGM’s systems being offline for weeks, during which time guests experienced delayed check-ins, non-functional slot machines, and manual cash payouts by pit bosses. This attack ultimately cost the entertainment giant over 130 million dollars. Their competitor, Caesars, faced a similar attack a week earlier and chose a different approach, reportedly paying $15 million to the attackers to prevent their customer data from being leaked.
This breach resulted in MGM’s systems being offline for weeks, during which time guests experienced delayed check-ins, non-functional slot machines, and manual cash payouts by pit bosses. This attack ultimately cost the entertainment giant over 130 million dollars. Their competitor, Caesars, faced a similar attack a week earlier and chose a different approach, reportedly paying $15 million to the attackers to prevent their customer data from being leaked.
Similarly, the Los Angeles Unified School District (LAUSD) experienced a ransomware attack in 2022 that compromised sensitive student data, causing widespread panic and necessitating costly mitigation efforts. Change Healthcare, a major healthcare technology company, also fell victim to ransomware, highlighting the vulnerabilities in the healthcare sector’s digital infrastructure.
In all of these examples, the organization lacked the proper resilience plan, experience, and infrastructure to ensure it could continue its business operations in the face of digital disruption. Unplugging systems as a reaction to such attacks is not a sustainable strategy. Instead, organizations need to adopt a proactive approach to cybersecurity involving continuous real-time monitoring, robust access controls, and stringent adherence to security best practices. By doing so, they can minimize the attack surface, enhance their ability to detect and respond to threats effectively and ensure business continuity.
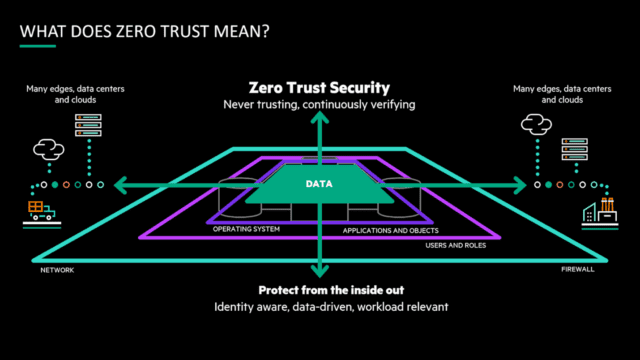
Don’t Trust, Always Verify
For decades, cybersecurity operated on the “castle and moat” principle. Everything outside the castle walls (the organization’s network) was considered untrusted, while everything inside was trusted. This strategy assumes that threats come from outside the organization and that internal systems and users are safe once past the perimeter. This assumption is dangerously outdated. Modern cyber threats are more sophisticated and can easily penetrate traditional defenses. Attackers often exploit seemingly minor weaknesses such as an employee’s weak password or a lack of MFA, gaining initial access and then moving laterally within the network or system to find valuable data or control critical systems.
That MGM Resorts breach highlighted this very approach. Hackers used social engineering to deceive MGM’s tech support into granting them legitimate access. Once inside, they moved freely across multiple systems and environments, causing significant disruption.
Modern threats can also originate from within the organization. Insider threats, whether malicious or accidental, can bypass external defenses and wreak havoc from the inside. The outdated, traditional perimeter-based security model fails to address the complexities of modern threats, where attackers can easily bypass perimeter defenses through phishing, social engineering, or exploiting vulnerabilities in trusted devices and, most commonly, through humans.
The cybersecurity paradigm must shift to a Zero Trust model to address these challenges. Zero Trust assumes no implicit trust, whether inside or outside the network. Every user, device, and application must be continuously verified before access is granted. This model is crucial today, where the workforce is increasingly remote and cloud services are ubiquitous. Zero Trust reduces the risk of lateral movement by attackers and ensures that security is enforced consistently across the entire IT environment.
By implementing Zero Trust, organizations ensure that only authenticated and authorized users and devices gain access to their resources, regardless of whether they are inside or outside the network. This approach minimizes the risk of breaches and limits the potential damage an attacker can cause once they gain entry.
Zero Trust operates on several key principles:
- Least Privilege Access: Users and devices are given the minimum level of access necessary to perform their functions. This reduces the risk of unauthorized access and limits the potential impact of compromised accounts.
- Continuous Monitoring and Verification: Trust is never assumed and is continuously verified through real-time monitoring and adaptive security measures. This ensures any suspicious activity is quickly identified and mitigated.
- Micro-Segmentation: The network and workloads are divided into smaller, isolated segments to prevent attackers’ lateral movement. This means that even if an attacker gains access to one segment, they cannot easily move to another.
- Multi-Factor Authentication: Implementing MFA adds an extra layer of security to verify the credentials of the person requesting access, making it more difficult for attackers to gain access using stolen credentials.
- Comprehensive Visibility: Maintaining a detailed view of all network users, devices, and activities within the network helps detect and respond to threats more effectively.
 Introducing the NIST Cybersecurity Framework 2.0
Introducing the NIST Cybersecurity Framework 2.0
The National Institute of Standards and Technology (NIST) Cybersecurity Framework 2.0 provides a comprehensive guideline for organizations to manage and mitigate cybersecurity risks, aligning with zero-trust principles. This updated framework emphasizes five key functions: Identify, Protect, Detect, Respond, and Recover.
- Identify: Understand and manage cybersecurity risks to systems, assets, data, and capabilities.
- Protect: Develop and implement safeguards to ensure the delivery of critical infrastructure services.
- Detect: Develop and implement activities to identify the occurrence of a cybersecurity event.
- Respond: Develop and implement activities to take action regarding a detected cybersecurity incident.
- Recover: Develop and implement activities to maintain resilience plans and restore any capabilities or services impaired by a cybersecurity incident.
By aligning with the NIST Cybersecurity Framework 2.0, organizations can build a robust cybersecurity posture that adapts to evolving threats and regulatory requirements.
XYPRO and HPE Address Ransomware Protection
Despite their reputation for reliability and robustness, ransomware attacks can absolutely target HPE NonStop systems. These systems are not immune to sophisticated cyber threats and abuse of privileges by malicious insiders. Attackers can exploit vulnerabilities through various means, such as social engineering, unpatched software, weak authentication, and misconfigured or improperly monitored systems. Once they gain access, ransomware can be deployed in a variety of ways, including introducing new malicious objects or modifying existing system assets. This will encrypt critical data, disrupt operations, and allow the attackers to demand hefty ransoms for decryption keys.
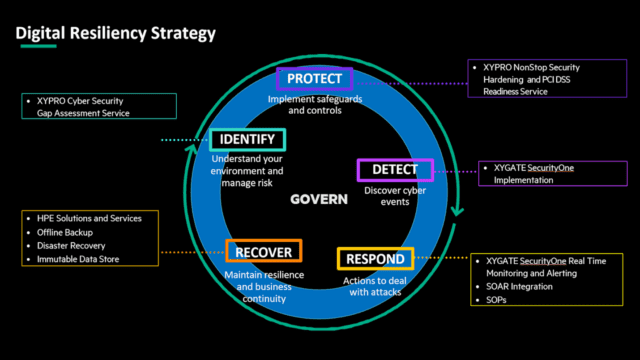 To effectively protect HPE NonStop systems from ransomware and other cyber threats, adopt a comprehensive security strategy aligned with Zero Trust principles. Below is a primer on where to start and how XYPRO and HPE help at each stage of the NIST Cybersecurity Framework:
To effectively protect HPE NonStop systems from ransomware and other cyber threats, adopt a comprehensive security strategy aligned with Zero Trust principles. Below is a primer on where to start and how XYPRO and HPE help at each stage of the NIST Cybersecurity Framework:
Identify – Gap Assessment and Asset Identification:
The first and most crucial step in this journey is to start with identification. You wouldn’t build a structure without first measuring, identifying the required materials, and measuring again. How can you protect your enterprise without identifying all the components and their risk? Performing a gap assessment is fundamental. XYPRO’s Cybersecurity Gap Assessment Service discovers, categorizes, and prioritizes your assets in preparation for a proper security implementation. This assessment identifies all assets, understands the current security posture and risks, and maps out the attack surface. No vendor tool can solve cybersecurity challenges without first completing this fundamental identification phase. Without a clear understanding of the existing assets and vulnerabilities, it’s a very difficult task to implement effective security measures.
- Identify Assets: Understanding what assets are present within the HPE NonStop environment is critical. This includes software, data and its locations, user accounts, network connections, and more. Identifying these assets recognizes where critical data resides and which systems are essential for business operations.
- Map the Attack Surface: Once assets are identified, it’s crucial to map out the attack surface. This involves understanding how these assets are interconnected, where potential vulnerabilities lie, and how an attacker might exploit them. This mapping provides a clear view of the security gaps and what needs to be addressed.
- Create a Roadmap: The gap assessment creates a detailed roadmap for implementing Zero Trust principles. This roadmap outlines the steps to secure the environment, including hardening the system and its applications, improving monitoring, and implementing robust response mechanisms.
Protect – Implementing Security Controls and Best Practices
- System Hardening and Application Security: Ensuring all systems are configured according to industry best practices is essential. This includes proper Safeguard configuration, system and application hardening, and disabling unnecessary services and ports to minimize the attack surface. Regularly updating and patching all software and firmware to address known vulnerabilities is crucial. Conducting regular security assessments of applications to identify and fix vulnerabilities must be a necessary and ongoing requirement. XYPRO’s System Hardening Service will implement best practices and remediate findings based on the identification phase and the roadmap created.
- Access Controls and Identity and Access Management (IAM): To establish strong access controls and IAM, implementing Role-Based Access Control (RBAC) ensures users have the minimum level of access necessary to perform their job functions. Regularly review and update roles and permissions. Enforce MFA by installing and configuring XYGATE User Authentication (XUA) for all users, especially for privileged accounts. Installing and configuring XYGATE SecurityOne (XS1) Access Control and Object Security applies the least privilege principle to limit user access rights and permissions to the bare minimum necessary for their tasks. Additionally, connect to Privileged Access Management (PAM) solutions like CyberArk to vault and control the use of privileged accounts, ensuring that administrative access is tightly controlled and audited.
- Implementing Findings from the Gap Assessment: This step implements findings from the gap assessment and prioritizes and remediates identified vulnerabilities by applying patches, updating configurations, or implementing new security measures. It also improves system monitoring and logging to ensure that all activities are tracked and anomalies are detected in real-time.
Detect – Real-Time Monitoring and Threat Identification
The Detect phase is critical for identifying and responding to potential threats in real-time. This phase involves continuous file and system integrity monitoring, advanced analytics, and immediate identification of suspicious activities. By implementing robust detection mechanisms, organizations can quickly recognize and mitigate threats before they cause significant damage. This phase can only properly be implemented after the identification and protection phase. On HPE NonStop systems, XYGATE SecurityOne (XS1) is the first and only solution for comprehensive real-time monitoring and ransomware detection that provides:
- Continuous Monitoring and Advanced Threat Detection Tools: XS1’s threat detection capabilities provide continuous real-time monitoring of all activities within the HPE NonStop environment. This ensures that any suspicious or anomalous behavior is immediately flagged for investigation, including potential intrusions or suspected ransomware and viruses. XS1 integrates with SIEM solutions like Splunk and others to collect, analyze, and correlate security events from various sources. This identifies complex attack patterns that may not be evident through isolated, binary, or threshold-based alerts.
- User and Behavioral Analytics: Analyzes normal user and system behavior and identifies deviations from typical patterns, which may indicate compromised accounts or insider threats. Using complex event processing algorithms to detect anomalies in data and user behavior, XS1 identifies potential threats that traditional detection methods might miss.
- Automated Threat Detection and Response Coordination: Every installation comes with automated alerts for predefined threat conditions. These alerts can be sent to security teams for immediate action, ensuring a swift response to potential threats. Correlation rules link related security events, providing a clearer picture of potential attack scenarios. This helps in understanding the broader context of an incident. This data helps with Incident triage of detected threats and ensures that the most critical threats are addressed first.
Respond – Swift and Effective Incident Management
This phase focuses on the actions to address and mitigate the impact of detected cybersecurity incidents. Effective response mechanisms are crucial to limit damage, reduce recovery time, and ensure continuity of operations. The sooner a ransomware attack is detected and responded to the faster and more cost-effective recovery will be.
- Automated Tools and Processes: Quickly isolate affected systems to prevent the spread of ransomware or unauthorized access. This containment strategy is vital in stopping an attack from compromising additional systems or data. Immediately revoke compromised credentials to prevent further unauthorized access. This includes disabling user accounts, changing passwords, and updating access tokens. Real-time alerts and notifications ensure the right teams are promptly informed of potential breaches and can take swift action.
- Incident Response Plans: Create detailed incident response plans that outline specific steps to take during different security incidents. These plans should cover detection, containment, eradication, recovery, and post-incident analysis. Regularly rehearse and conduct drills to ensure that the response plans are effective and that all team members are familiar with their roles and responsibilities. Simulated attack scenarios can help identify gaps and improve response strategies. Establish clear communication protocols for internal and external stakeholders. Ensure that key personnel are informed promptly and provide transparent updates to customers and partners as needed.
- Coordinated Response and Recovery: Implement a coordinated approach to incident response involving cross-functional teams, including IT, security, legal, and communications. This ensures that all aspects of the incident are addressed comprehensively. Conduct a thorough forensic analysis to understand the nature and extent of the breach. This helps identify the root cause, determine the impact, and prevent future occurrences. Execute remediation actions to eradicate the threat, such as removing malware, patching vulnerabilities, and restoring affected systems from backups. Ensure all systems are thoroughly cleaned and secured before returning to normal operations.
The Path to Robust Security
Ransomware and other cyber threats are evolving faster than ever. The availability and affordability of cloud environments and AI/ML-based systems for cyberattacks are becoming commonplace. Adopting a proactive and comprehensive approach to cybersecurity is imperative. Moving away from outdated strategies and embracing Zero Trust and the NIST Cybersecurity Framework 2.0 are critical steps to remain resilient and operational.
XYPRO and HPE’s approach to cyber resilience goes beyond protection. Our solutions ensure that organizations can survive and recover from cyber disruptions, maintaining business continuity, even in the face of sophisticated attacks. Following a structured and thorough approach to cybersecurity, including regular assessments and updates, helps organizations stay ahead of emerging threats and ensure their systems and data remain secure.
The path to robust cybersecurity and digital resilience involves adopting modern security frameworks, implementing comprehensive protection measures, and leveraging the expertise of trusted partners like XYPRO and HPE. By doing so, your organization can confidently navigate the complex threat landscape, knowing you have the solutions, strategies, and experienced partners to protect, detect, respond, and recover from cyber threats.
Originally published on Xypro’s website July 15 2024


Be the first to comment