
Introduction
In today’s world of round-the-clock online business and commerce, data is everywhere. Data has become your superpower, even more so when it’s protected data.
As many users of HPE NonStop systems are processing a large amount of sensitive or mission-critical data it is paramount that such data is protected in the best possible manner.
The challenge that many organizations are facing is that the isolated databases of old have evolved dramatically and so has the need for appropriate data protection and security.
The Challenge
Not too long ago, things were nice and simple: Organizations built perimeter defences like firewalls, network intrusion detection and network access controls around their systems to protect their databases containing sensitive data.
Over time, with more and more digital channels evolving, data sources started to shift outside the perimeter. Organizations started to punch small holes into the perimeter to accomodate connectivity with these new digital channels and data sources. In addition, organizations have started to shift huge amounts of data outside the perimeter, into the cloud and this trend will continue with many companies executing ‘cloud only strategies’.
IoT (Internet of Things) use cases are leading to even more data being created outside the perimeter.
Lastly, data exchange with business partners also puts the data beyond the control provided by the perimeter. All these developments have made it increasingly harder to control, manage and secure the data.
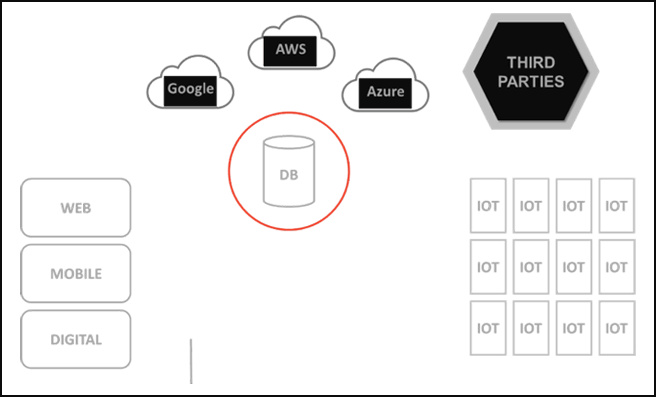
Figure 1 – Increasing number of data sources and channels
If we add this all up, it becomes clear that there is no perimeter security anymore. Instead, we are looking at a complex architecture that even crosses organizational boundaries.
Let‘s look at what happens with sensitive data in such an architecture:
-
- First, the data is created – for example in a web application or by an IoT device. The sensitive data starts to move through an organization‘s network where it is processed and analysed. Sensitive data continues to spread further – into the cloud.
- Sensitive data is often shared with business partners as well. At this point, the sensitive data has spread across the whole architecture, potentially unprotected, and is now posing a serious risk.
- Organizations are not only facing security risks, they also need to comply with industry regulations and data privacy laws that require them to protect sensitive data or face serious fines.
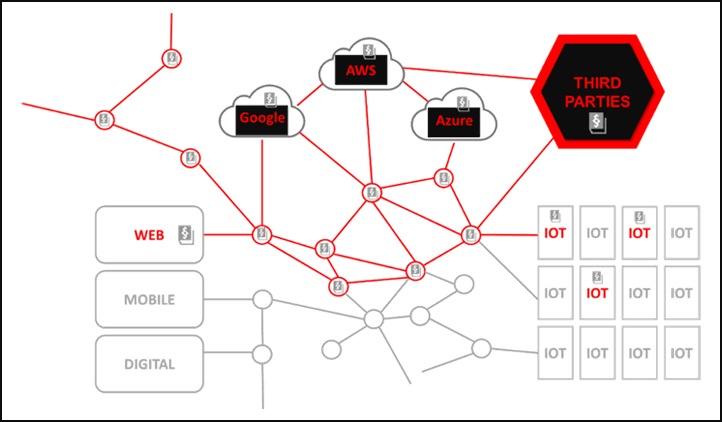
Figure 2 – Sensitive data travelling across the organization and channels facing additional regulatory pressure
But how do you protect your sensitive data that travels inside and outside your organization while at the same time trying to comply with regulations and data privacy laws like GDPR in Europe and CCPA in California for example?
How do you solve the conundrum? The solution.
There are two key principles when it comes to protecting your data effectively:
-
- Protect data at the earliest possible point – start protecting the data where it is being created, i.e. at the application layer. The data is then protected as it travels around your organization and as you share it with external parties.
- De-protect only when absolutely necessary – very few business functions and people need access to the real data. Most data analytics and business intelligence tasks can be performed without the original data as long as data integrity is provided.
In light of these two principles, what are the predominant data security options of protecting data?
-
- Volume Level Encryption (VLE) – VLE only protects you against the physical risk of someone trying to steal your hard disk. In most cases, as mentioned above, this level of security is not enough.
- Classic encryption – This is a good protection method, but the encryption algorithm turns the data into a string of unuseable data and everytime you want to move, use or analyze the data, you have to decrypt it first.
- Data masking – Data Masking allows you to process sensitive data while it‘s still protected, but it significantly limits the useability of the data for data analytics. Once data is masked it is rather difficult to reverse the masking of the data.
- Tokenisation or format-preserving encryption – These two options give you the best of both worlds: They provide strong data-centric protection that travels with your data, while keeping the characteristics and structure of the data elements in tact. The data can still be used by applications, which rely on its format for processing and it can be used for data analytics – all without having to de-protect the data.
As data-centric security gains mainstream recognition for its ability to protect sensitive data against theft and malicious use, enterprises are faced with choosing a solution from an increasing array of options. The key requirements for a true data-centric implementation that need to be considered are:
-
- Ease of integration – the best security solution is worth nothing when it doesn’t integrate in your existing infrastructure and is not sustainable. To minimize implementation effort and avoid the cost and time to change existing applications, look for a solution that offers flexible integration with existing tools as well as future projects and adapts to new technology and infrastructure as it emerges. Both native and API-based integration need to be taken into account.
- Linear scalability – Modern infrastructure increasingly includes processing and analysis of streamed / real-time data. You need a security solution that can keep pace. To make the most of your data, whether it’s real-time or historical, your data-centric security solution should easily scale as your workloads scale, with no performance impact.
- High performance – More solutions are now using artificial intelligence capabilities and taking advantage of in-memory data processing. To keep up with the speed and performance requirements of these systems, look for a data-centric security solution that delivers high performance with features such as intelligent streaming and load distribution.
- High availability – Security shouldn’t impact the availability of your environment. Choose a solution with built-in fault tolerance so that any unexpected failures are resolved automatically without interruption of service.
- Support for multicloud and hybrid environments – You need a solution that supports your current and future environment, whether that’s on-premises, in the cloud, or a hybrid of both.
While the typical payment processing application on HPE NonStop may not have many touchpoints in the cloud or with partner systems today, it is this very payment application, which creates massive amounts of sensitive data. That sensitive data needs to be protected at the earliest possible point (data protection principle 1 above) which puts the HPE NonStop platform in the centre of your data-centric data protection strategy.
Summary
As the challenges and risks from ever-increasing amounts of data in the enterprise grow exponentially and at the same time organizations are facing more pressure from internal and external security audits and data privacy regulations, the need for an effectice data-centric protection increases as well. As outlined above, the most elegant and effective method of protecting your sensitive data is a tokenization solution, which allows organizations to take control of their sensitive data and to perform all business intelligence and data analytics functions across the enterprise and beyond.
Data is your superpower!



Be the first to comment