
 Does a corporation have the sole responsibility of protecting its user’s data?
Does a corporation have the sole responsibility of protecting its user’s data?
There are several different factors to consider when thinking about protecting your data. The subject can be complex and usually involves multiple parties.
Let’s begin with a simple thought exercise. Think about how much personal information you share on a day-to-day basis, online or otherwise. Consider who and what you interact with; applications, devices, websites, humans, corporations, etc. How much time do you spend thinking who has access to your data and what they could do with it? What are some of the things that you do to ensure you are protecting your valuable information?
Let me ask you this: who is responsible for securing your personal information? The answer might be obvious; you are responsible for securing your own data and ensuring it is not being used incorrectly or being shared with unknown or unwanted third parties.
So what happens when we move this thought exercise to the corporate world? You quickly realize that the amount of personal data being used by an organization during normal operations becomes staggering, almost unfathomable. Keep in mind that many people within a corporation can potentially have access to sensitive information, not to mention the potential for outside users to access these same assets, unassisted or otherwise.
Of course, it is understood that corporations invest countless resources on matters regarding their data security. IT administrators install the latest antivirus software, raise firewalls, deploy encryption technology, and also periodically run vulnerability tests. But are they the only ones responsible for a company’s data security and protecting a user’s data?
How much responsibility do other internal users have in protecting the information? Even if you employ all of the procedures mentioned above, every single user in your organization is a potential entry point for hackers.
It is clear that corporations and individual users have a shared responsibility in securing personal information. An organization can have the most effective data security strategy, employ the best IT security personnel and deploy the most advanced security technologies available, but if an individual user is careless with how they access this information, it becomes a foundational weakness, one that can also be exploited.
 What are some of the most significant threats that an organization faces when handling your information?
What are some of the most significant threats that an organization faces when handling your information?
The highly respected cybersecurity firm Symantec published the “Internet Security Threat Report” in February 2019. You can read the full report here (fair warning, you will not be sleeping well tonight!) but these are some of the report’s “highlights” (“frightlights”; can we make this a thing?) for 2018:
Messaging Attacks
- 48% of malicious email attachments in 2018 were MS Office files; up from 5% (!) in 2017.
- Employees of small organizations were more likely to be hit by email threats—including spam, phishing, and malware—than those in large organizations.
- 55% of emails received in 2018 were categorized as spam.
- In 2018, 1 in 3,207 emails was a phishing email.
- Microsoft Office users are the most at risk of falling victim to email-based malware.
Mobile Attacks
- 1 in 36 mobile devices used in organizations was classed as high risk or had high-risk applications installed. This included devices that were rooted or jail-broken, along with devices that had a high degree of certainty that malware had been installed.
- Mobile ransomware infections increased by 33% from 2017
- The U.S. was the country worst affected by mobile ransomware (63% of all infections), followed by China (13%) and Germany (10%).
Web Attacks
- In 2018, 1 in 10 URLs analyzed was identified as being malicious, up from 1 in 16 in 2017.
- Web attacks on endpoints increased by 56% in 2018.
- By December 2018, more than 1.3 million unique web attacks on endpoint machines were being blocked every day.
- Formjacking (the use of malicious JavaScript code to steal payment card details and other information from payment forms on the checkout web pages of eCommerce sites) was one of the biggest cybersecurity trends of the year.
- On average, 4,800 websites were compromised via formjacking code every single month in 2018.
- More than 3.7 million formjacking attempts on endpoint devices were blocked in 2018.
How can you effectively secure access to systems and personal information?
Now that we’ve recognized that data protection is a joint responsibility between an organization and individual users, and established the types of threats being faced in today’s cybersecurity environment, let’s discuss what can be done to ensure that personal information is being protected. We understand that these measures are not always fool-proof, but there are important steps that can be taken to improve data security. You should also consider the “best practices” when implementing these security measures.
Identity theft is a low-risk/high-reward type of crime for hackers; this makes it a real threat to all businesses. As detailed previously, weak passwords can lead to stolen credentials. Weak credentials are one of the easiest ways for hackers to compromise a system or application; this is why the majority of web application attacks begin with stolen credentials.
Users have a responsibility to protect their data. Many steps can be taken to ensure personal information is kept safe, including the use of strong passwords, the use of a mobile password manager to help keep passwords strong and unique across all of devices and accounts, locking applications when not in use and signing out of accounts not being used.
Corporations must also employ diverse measures to ensure data security for their users. These include ensuring the latest operating system updates are installed, backing up data, and encrypting data. As previously established, anti-virus systems and advanced firewalls are necessary security elements, as are vulnerability tests. Without user authentication though, the proverbial “front door” is left wide open to intruders. The sobering reality is that, even with strong password requirements, if multi-factor authentication (MFA) is not in place, these other security measures can easily be bypassed. Additionally, some of the modern MFA applications available today also include reporting capabilities, which ensure that compliance standards, such as PCI DSS, are being met.
The ability to verify a user’s claimed identity through various authentication factors has become crucial for NonStop systems, especially for users that will be logging-on to business-critical applications. Fortunately, most users have already become accustomed to authenticating themselves in their daily lives. Providers of online services such as banking, gaming, social media, and email now include tools that effectively authenticate users when accessing their systems.
IT managers should categorize their systems to identify those that contain access to business-critical user data; they can then add MFA on top of those systems. MFA has low complexity, which makes it an easy addition to an organization’s security strategy. It can also be rolled out quickly without busting the budget.
Ineffective authentication comes with significant direct and indirect risks, including compliance penalties, data theft, loss of customer trust, and significant loss of revenue. There is an over-reliance on insecure forms of authentication, such as passwords and security questions, this can lead to security gaps that create opportunities for intruders.
Modern authentication methods represent a more robust security structure, and also provide a better user experience when logging into applications. MFA also makes it easier for auditors to get answers to critical compliance questions; providing information such as which users are granted access to which system, and also how the access policy is being reliably enforced.
Prevent fraud with Multi-factor Authentication
Multi-factor authentication has become vital in ensuring secure access to systems and other valuable resources. It provides superior safety measures when attempting to access systems and financial applications, and is also an important requirement to comply with regulations such as PCI 8.3 and GDPR. MFA prevents access to phishing websites or spoofing applications, the added security layers provided by MFA help to keep you from falling for these types of traps.
As a result of PCI DSS 3.2, any application that has access to the cardholder environment must include Multi-Factor Authentication. From legacy NonStop applications to the latest RESTful interfaces, effective MFA must be provided for users and applications that have the potential to access these environments.
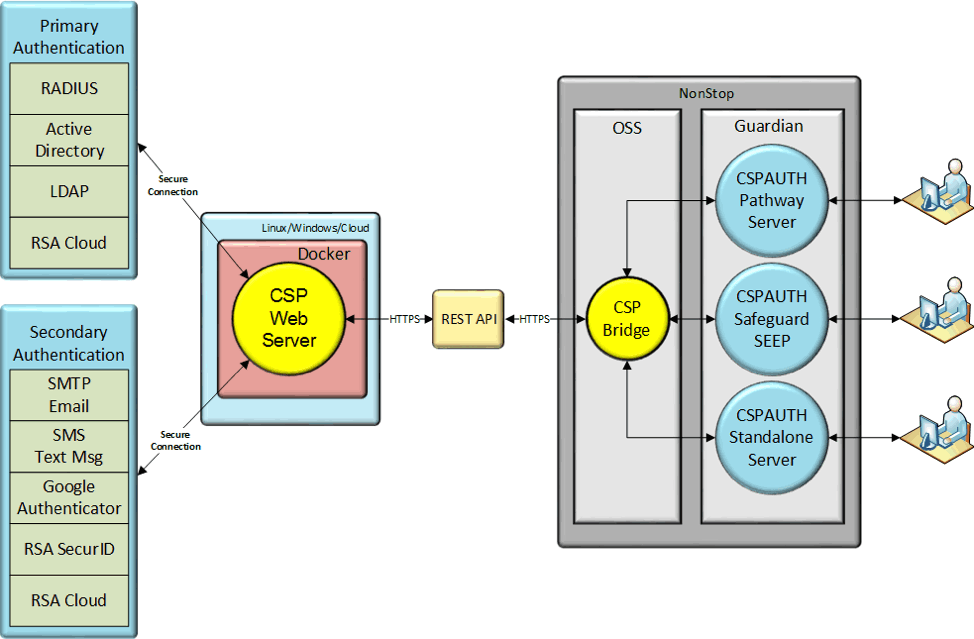
CSP Authenticator+™ supports both primary and secondary authentication for NonStop. It provides a RESTful interface that supports multi-factor authenticated logins on NonStop systems. CSP Authenticator+ resides on the NonStop Platform and uses an OSS “bridge” to connect to the RESTful interface of the CSP Authenticator+ web server.
Primary authentication methods such as RADIUS, RSA Cloud, Active Directory, and Open LDAP are supported; User Rights Synchronization will also make it easier than ever before to integrate a NonStop system into the Enterprise ID management platforms.
CSP Authenticator+ can provide authentication services via Safeguard Authentication SEEP, or Pathway and Non-Pathway servers. Almost any application, including TACL, can now easily support multi-factor authentication (MFA).
CSP Authenticator+ Key Features:
- Primary and Secondary authentication support
- Browser-based user friendly interface
- Standardized authentication across platforms
- Configurable for all or selected users
- Support for virtual addressing
CSP – Compliance at your Fingertips™
For complimentary access to CSP-Wiki®, an extensive repository of NonStop security knowledge and best practices, please visit wiki.cspsecurity.com


 We Built the Wiki for NonStop Security ®
We Built the Wiki for NonStop Security ® 
Be the first to comment