
I used to think that applying security is good as long as it does not get in the way of productivity. After all, isn’t the whole purpose of IT to improve productivity, so anything going against that golden rule is at least questionable? If security is an obstacle to productivity then it defeats the whole purpose of IT being at the service of humans and it should not be the other way around. But don’t get me wrong, I have never neglected security. Back in 2004, I was co-presenting at ITUG with Thomas Burg from Comforte and Carl Weber from GreenHouse: “How to Harden Your NonStop Server: A Security Show and Tell “. I always tried to adopt good security practices such as not using SUPER.SUPER for day to day tasks back in my years in support. And when PKI came out I really worked hard on understanding the details of the conversation between Alice and Bob. In summary, I considered security important and a necessary feature but somewhat second in my own imaginary priority list. This was 10 to 20 years ago.
 A 3 hours marathon on security back in 2004. We miss you, Thomas.
A 3 hours marathon on security back in 2004. We miss you, Thomas.
Today, however, a lot has changed and I’m personally revisiting that priority list. First, we work remotely, this means access to systems has to be made available via Internet, through firewalls, with tunneling such as SSH and others. Data flows all over, between public and private clouds, with some applications relocating in one or more public clouds, multiple geographic locations, using shared governance with service providers. And maybe, more importantly, data is an increasingly vital asset for companies, sometimes a currency that is a target from not only the proverbial “malicious user” which almost sounds like a friendly relatively unthreatening term but also from larger groups, organizations, or even foreign governments. Today many of those security breaches turn into ransomware with the potential to take companies down to their knees, bring public infrastructures to a halt, and even endanger people’s lives. In that context, the term “malicious user” sounds like a symptom of denial of the real severity of the problem at hand. I think what has changed is that there is simply too much at stake with our data today. Unfortunately, as counterintuitive as it seems, I’m afraid productivity may now have to take second place. Can anyone afford to not protect its own data, put at risk its own enterprise’s data and be the weak link that was exploited by hackers?
In the end, it will always be a balancing act. Planning to use all our arsenal of security features, right from the start, is the least we can do. Maybe a shift in mindset is necessary. Recognizing for example that it is, in general, easier to increase productivity after security rules are in place than it is to impose security rules after users have been acquiring and ingraining their personal best practices. Do we even find it an issue to require a key to open our car? But what if we have to start entering a password to start the GPS in that same car? It is not easy to get user acceptance but as weaknesses of security gain more public awareness, such as, for example, password brute force attacks, then the counter measures such as multi-factor authentication becomes more easily accepted. Automation, a common practice in the cloud, is also likely an interesting avenue to find a good compromise in many places.
NonStop has not buried its head in the sand and as it is often the case has been carrying a leading effort in this area for a long time. We have a long history of integrating security features right from the start in our product designs but also getting help from partners to address needs from that vast technology domain. Our record speaks for itself with a marginal number of platform-specific CVSS-defined vulnerabilities found over the years when compared to Microsoft and Linux operating systems. Our unique NonStop architecture is also the gift that keeps on giving, as it is simpler to secure a single system image, than a multitude of separate, assembled nodes, using a long list of differently sourced software with seriously disparate levels of security.
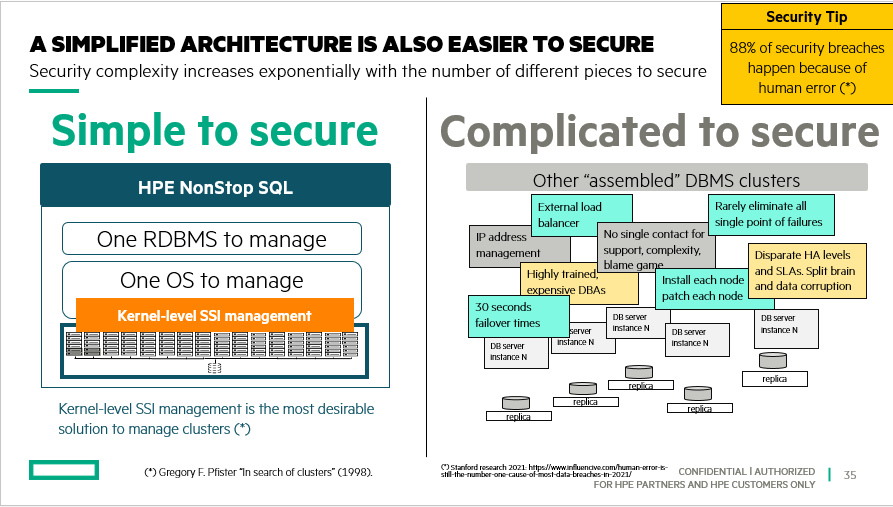
NonStop Single system image, the gift that keeps on giving
So what should be our next step? I think first we need to recognize that things have changed enough that maybe we need to rethink not only our priorities but also our choices of tools and methods when it comes to that balancing act between security and productivity. First, know what’s in your arsenal of security features. This year at NonStop NonTBC we’ve offered many talks on security including a brand new talk TBC21-403 Securing Your Data in NonStop SQL and whose contents are also now part of our L21.11 refresh of the HPE NonStop security hardening guide.
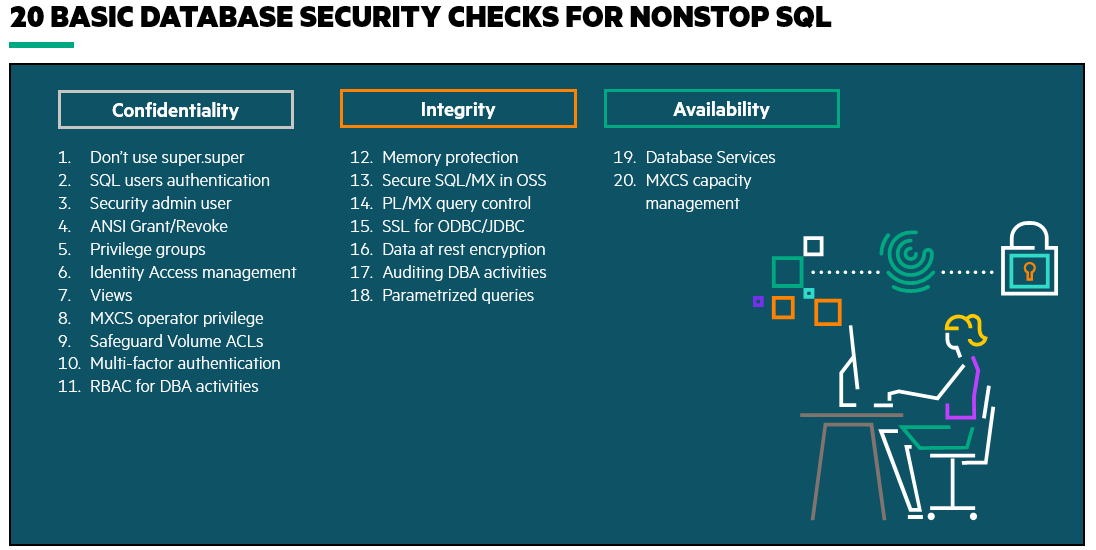 TBC 2021: Securing your data in NonStop SQL presentation
TBC 2021: Securing your data in NonStop SQL presentation
Then we may want to start reducing the number of tools we need to use, simplifying the security scheme to be put in place, eliminating software that does not implement good enough security. As we know, security is a journey, not a destination. Simplifying therefore goes hand in hand with increasing your chances to successfully keep your data secured. Ensure we change or enforce best practices and policies, such as adopting the principle of least privilege using RBAC (Role-Based Access Control), auditing to detect, analyze and avoid security breaches and using strong security alerts systems to streamline and simplify security.
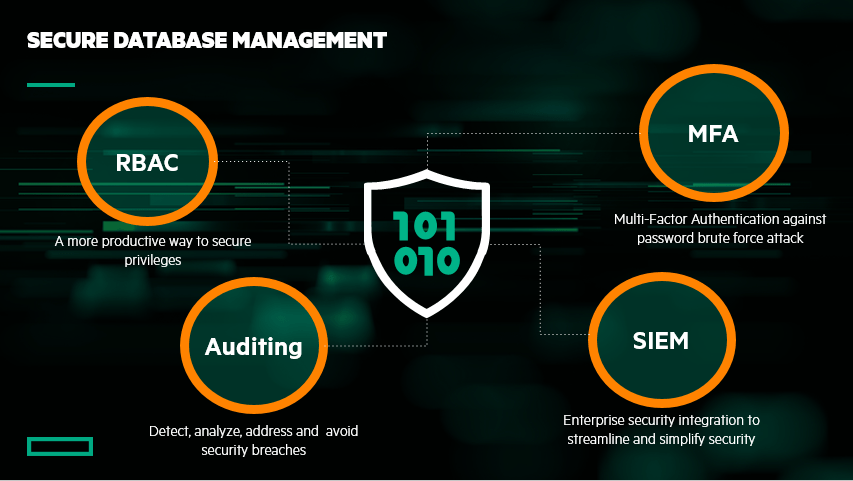
TBC 2021: Secure Database Management demo
The key to implementing the balancing act? I believe it starts with the knowledge of common threats and what their countermeasures are. Then, ensure your organization adopts those countermeasures. This may be the hardest task where weak user acceptance needs to be met with bold decisions and strong executive endorsement. In some cases, security and productivity will clash, priorities may shift, but with better information in hand, you can make the right decisions, and continue business as usual in a safer way.


Be the first to comment